- 587
User Authentication in n8n Workflows Using OpenID Connect
Securely authenticate users in n8n workflows. Benefit from easy integration and robust security features using OpenID Connect.
Securely authenticate users in n8n workflows. Benefit from easy integration and robust security features using OpenID Connect.
Who is this workflow for? Securely authenticating users is critical for workflows that interact with sensitive data or perform privileged operations. This workflow leverages OpenID Connect to authenticate users, ensuring that only authorized individuals can trigger webhooks and access protected resources within your n8n automation..
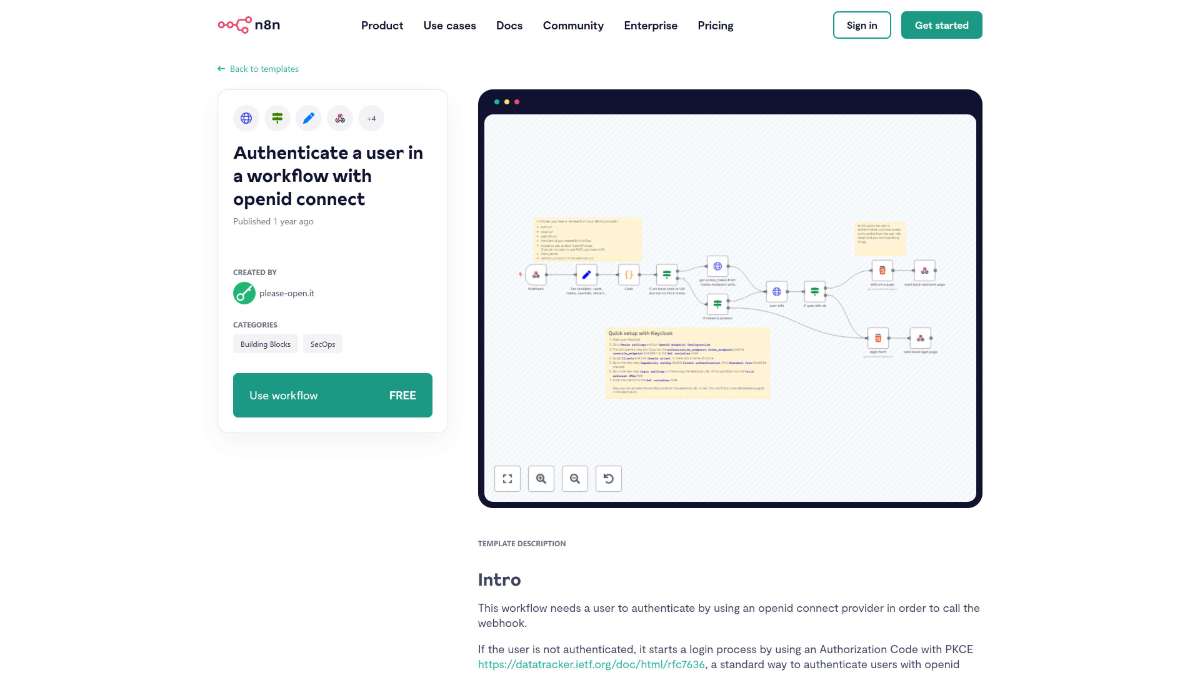
The workflow begins by requiring the user to authenticate via an OpenID Connect provider. If the user is not authenticated, the workflow initiates a login process using the Authorization Code with PKCE flow, a secure method outlined in RFC 7636.
Users are redirected to the identity provider’s authorization endpoint to log in. This step ensures that credentials are handled securely by the identity provider.
Upon successful authentication, the identity provider redirects back to the workflow’s webhook URL with an authorization code. The workflow exchanges this code for an access token and stores it in a cookie named n8n-custom-auth.
Using the access token, the workflow calls the userinfo endpoint of the identity provider to retrieve detailed information about the authenticated user. This information includes the user’s ID, email, and verified status.
With the user’s token and information securely obtained, the workflow proceeds to execute the intended webhook action. All subsequent requests within the workflow can utilize the user’s token for authenticated API calls.
The workflow is configured to work seamlessly with identity providers like Keycloak. Configuration involves setting up the OpenID Connect endpoints, disabling client authentication, and configuring valid redirect URIs to ensure secure token exchange.
After user login, the webhook refreshes and retrieves the user’s token from the cookie. This token is used for all API interactions, ensuring that each request is authenticated and authorized based on the user’s identity.
This workflow is ideal for developers and automation specialists who need to secure their n8n workflows by authenticating users before allowing access to webhooks and connected services. It is particularly useful for teams managing sensitive data or requiring granular access control based on user identities.
This n8n workflow template provides a secure and efficient method for authenticating users using OpenID Connect. By integrating with identity providers like Keycloak, it ensures that only authorized users can trigger webhooks and access protected APIs. Enhance your automation processes with robust user authentication and personalized API interactions, all within the flexible n8n environment.
For a deeper dive into this authentication flow and additional implementation details, visit our blog post.
Automate the import of Meta Threads posts into Notion. Streamline your workflow with seamless integration and efficient data handling.
Automate data entry and retrieval in Google Sheets. Use n8n to streamline processes, save time, and ensure accurate data management efficiently.
Automate error reporting to Slack for efficient workflow monitoring. Ensure timely notifications and streamline issue resolution with key integration features.
Help us find the best n8n templates
A curated directory of the best n8n templates for workflow automations.