- 634
URL and IP Threat Intelligence Lookup System with n8n
Strengthen security by automating URL and IP threat intelligence. Utilize real-time data analysis and integration in this efficient n8n workflow.
Strengthen security by automating URL and IP threat intelligence. Utilize real-time data analysis and integration in this efficient n8n workflow.
Who is this workflow for? Enhance your cybersecurity operations with this n8n workflow, designed to seamlessly integrate URL and IP lookups using GreyNoise and VirusTotal. Automate threat intelligence gathering to quickly assess and respond to potential security threats..
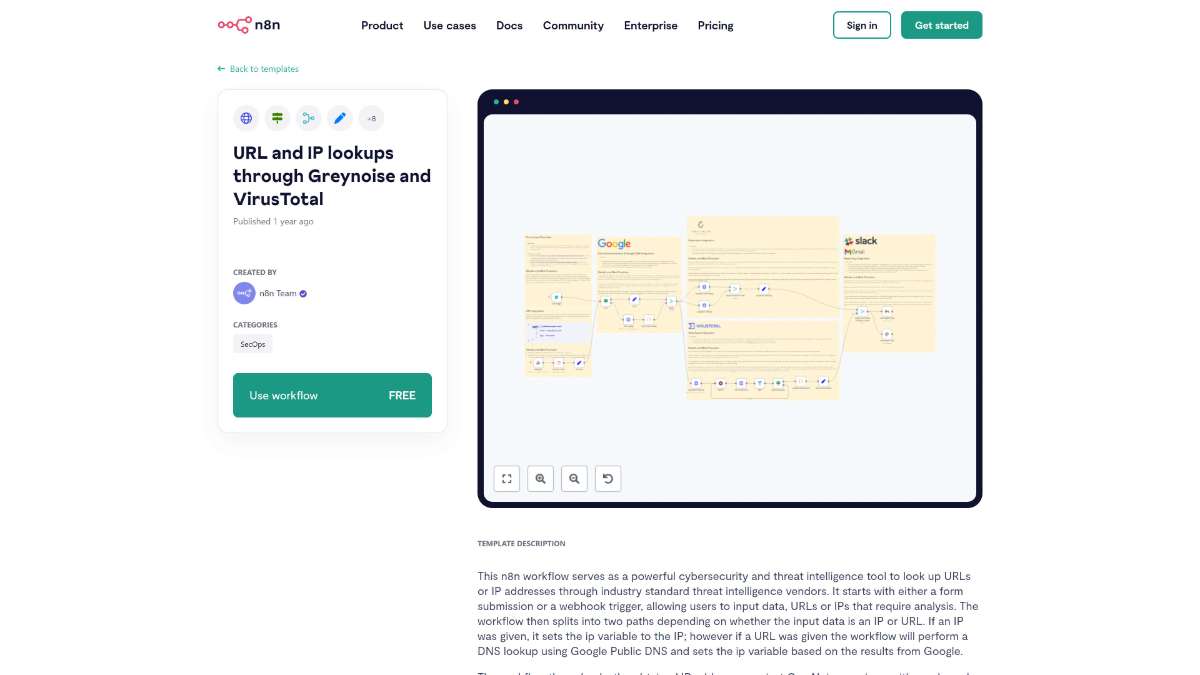
This workflow is ideal for cybersecurity professionals, IT administrators, and security operations centers (SOCs) seeking to automate and enhance their threat intelligence capabilities without extensive manual intervention.
This n8n workflow automates the process of analyzing URLs and IP addresses using GreyNoise and VirusTotal, providing comprehensive threat intelligence. By integrating seamlessly with notification platforms like Gmail and Slack, it ensures that relevant stakeholders receive timely and actionable security insights.
Improve AI agent analysis by integrating vector databases. Automate workflows and enhance data processing with this n8n template.
Streamline user setup in Vero using n8n. Automate tasks, reduce manual work, and improve efficiency with this powerful integration template.
Send daily birthday alerts to Slack, streamline notifications, and never miss a celebration with this efficient n8n workflow template.
Help us find the best n8n templates
A curated directory of the best n8n templates for workflow automations.