- 537
Automate Slack Notifications and Jira Ticket Creation for Quarantined Emails
Streamline communication by notifying Slack and auto-creating Jira tickets for quarantined emails, enhancing team responsiveness and issue tracking.
Streamline communication by notifying Slack and auto-creating Jira tickets for quarantined emails, enhancing team responsiveness and issue tracking.
Who is this workflow for? This n8n workflow automates the response to potentially malicious emails flagged by Sublime Security. It not only notifies the relevant users in Slack about quarantined emails but also creates detailed Jira tickets if the email has been opened, ensuring a streamlined incident management process..
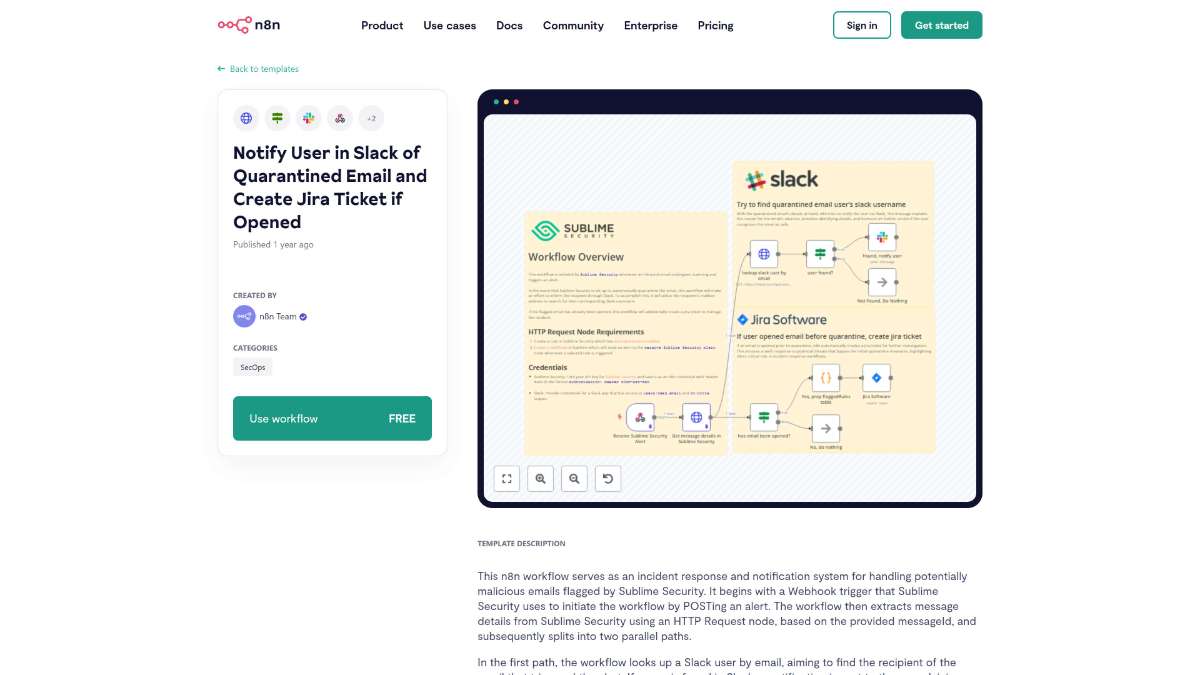
messageId.Slack Notification Path:
Jira Ticket Creation Path:
read_at timestamp from Sublime Security to determine if the email has been opened.This workflow is ideal for IT security teams, system administrators, and organizations that utilize Sublime Security for email protection and rely on Slack for team communication and Jira for issue tracking. It is designed for users seeking to enhance their email security incident response with automation.
This n8n workflow seamlessly integrates Sublime Security with Slack and Jira to enhance your email security incident response. By automatically notifying users of quarantined emails and creating detailed Jira tickets for opened incidents, it streamlines communication and ensures efficient tracking and resolution of potential security threats.
Streamline workflows by syncing Mautic contacts to Monday.com. Automate item creation and improve efficiency with this powerful n8n template.
Extract and store data efficiently with this n8n template, featuring automated multi-page scraping and seamless data integration.
Streamline data flow from Typeform to Google Sheets, Slack, and email. Enhance efficiency and keep your team informed with automated notifications.
Help us find the best n8n templates
A curated directory of the best n8n templates for workflow automations.