- 670
Automate Email Security Processing Using n8n and Sublime Security
Streamline secure email handling, enhance protection, and leverage automation with key features using this n8n and Sublime Security solution.
Streamline secure email handling, enhance protection, and leverage automation with key features using this n8n and Sublime Security solution.
Who is this workflow for? Streamline your email security operations with this n8n workflow designed to automatically receive and analyze email attachments. By integrating Sublime Security, the workflow ensures that your organization can proactively detect and handle potential threats with minimal manual intervention..
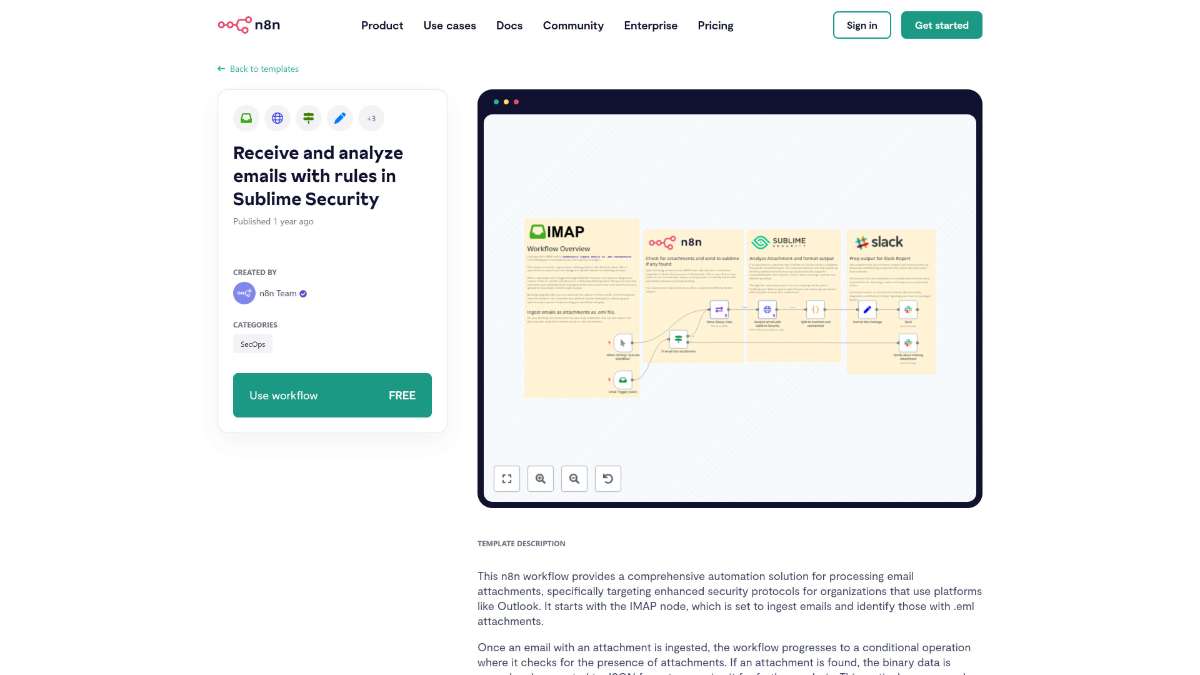
.eml attachments.This workflow is ideal for IT administrators, security professionals, and organizations that rely on email communication platforms such as Outlook. It is particularly beneficial for teams seeking to enhance their email security protocols without extensive manual processes.
This n8n workflow leverages Sublime Security to provide an automated, efficient solution for processing and analyzing email attachments. By integrating essential tools and streamlining security protocols, it enhances your organization’s ability to detect and respond to email-based threats swiftly and effectively.
Streamline playlist updates and organize content effortlessly with automated syncing from YouTube to Raindrop, ensuring seamless collection management.
Simplify lead collection with n8n's multi-form integration, enhancing data accuracy and workflow efficiency.
Streamline LinkedIn posting, enhance productivity, and manage content seamlessly with Notion integration using this automated n8n workflow.
Help us find the best n8n templates
A curated directory of the best n8n templates for workflow automations.