- 574
Analyze Email Headers for IP Addresses and Spoofing Detection
Uncover spoofing and identify IPs easily with this n8n template. Streamline email analysis and enhance security with automated header examination.
Uncover spoofing and identify IPs easily with this n8n template. Streamline email analysis and enhance security with automated header examination.
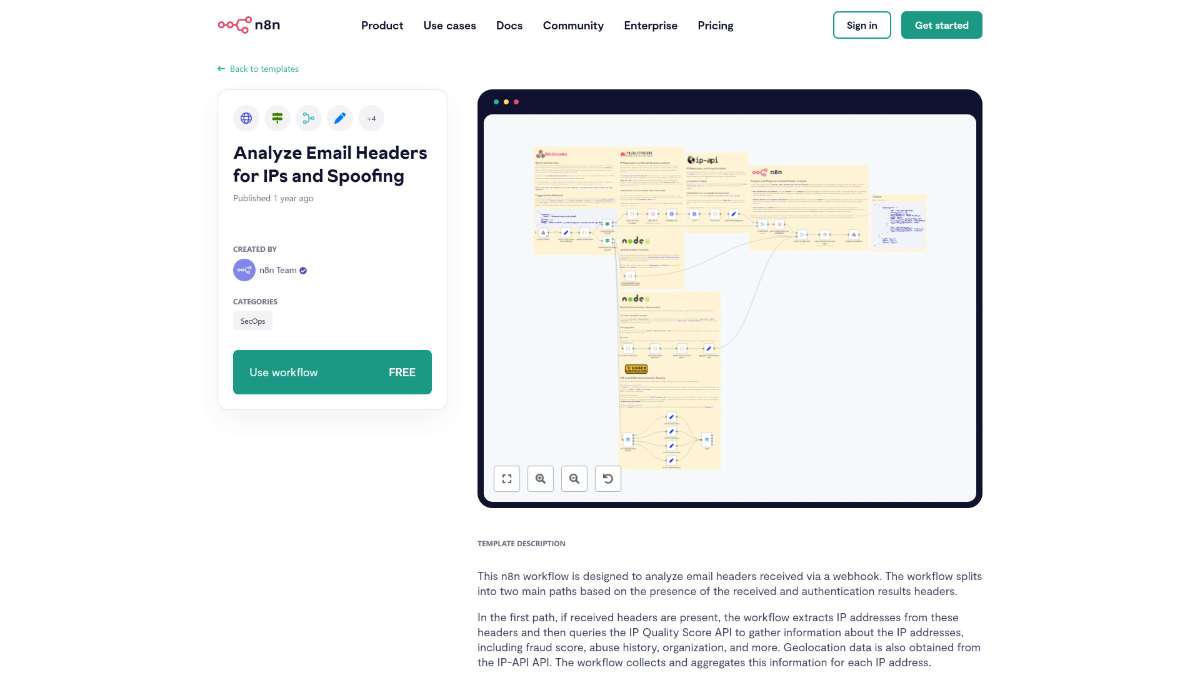
Who is this workflow for? This n8n workflow analyzes email headers received via a webhook to detect IP addresses and potential spoofing attempts. It efficiently extracts relevant header information, evaluates authentication results, and aggregates the data for comprehensive analysis..
This workflow is ideal for IT security professionals, email administrators, and organizations looking to safeguard their email communications. It suits those who need to monitor and verify the authenticity of incoming emails to prevent phishing and spoofing attacks.
This n8n workflow automates the analysis of email headers to identify IP addresses and evaluate authentication results, providing a robust solution for detecting spoofing and enhancing email security. By integrating with various APIs and platforms, it delivers comprehensive insights and facilitates proactive threat management.
Automate the creation of masked emails with Fastmail using n8n. Enhance privacy, streamline processes, and boost security effortlessly.
Streamline bug tracking by integrating Slack with Linear. Automate bug creation, reduce manual effort, and enhance workflow efficiency with n8n.
Discover visitor locations to enhance targeting. Utilize IP detection and uProc integration for accurate country identification in n8n.
Help us find the best n8n templates
A curated directory of the best n8n templates for workflow automations.